Security questions will always be insecure
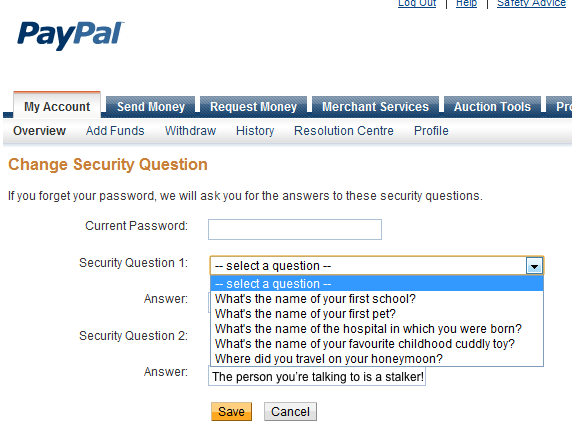
Would a real person on the other end accept this answer or escalate?
The purpose of insecurity questions and answers is to bypass not knowing the password. The more they’re treated like passwords, the more useless they become for that purpose.
Insecurity questions are those questions you’re forced to answer when you create an account just in case you forget your password. The answers are about some aspect of your life. Your mother’s maiden name. Your first date. Your most inspirational teacher. Your favorite actor.1 Public information that is hopefully obscure enough to identify you in the unlikely event that you forget your password, but at the same time keeping the mass of potential hijackers out.
Insecurity questions are sometimes called security questions, secret questions, out-of-wallet questions2, or knowledge-based authentication. These questions by their nature require awkward security tradeoffs. Sometimes I think the reason password recovery questions are referred to with misleading names like “security questions” and “secret questions” is to gloss over the fact that they are horribly insecure, not at all secret, and do little to ensure authentication. The questions aren’t secret. They’re shown to anyone attempting to bypass not knowing the password. The answers aren’t secret. That’s the whole point, that they are information about a person that the person won’t, like their password, forget.
Calling them security questions obscures the fact that they specifically reduce security. That’s their entire purpose: to provide alternative access to a protected service, in a way that doesn’t require knowing the account owner’s access credentials. The more avenues we provide for accessing a protected service without knowing or having the pass information, the easier it is for the hijacker. Two different access paths will always be less secure then one path, even if both paths are secure—and insecurity questions are by design not secure. That’s their whole point, that you’ve lost access to the secure path.3
It’s a lot like the old mystery schtick about only criminals having alibis. Who knows they’re going to need an alibi for 9 pm on Thursday night? The criminal who planned a crime for 9 pm on Thursday. The mass of people innocent of the crime have no idea they need an alibi, and apply no resources to creating one.
Most users don’t forget their password, and so will never have to go through the alternative access path. But the insecurity questions remain available to hijackers regardless. And because their entire purpose is to bypass not knowing the password, insecurity questions and their answers cannot be treated like passwords. This makes them perfect for hijacking an account.
And this leads into the second major issue that makes insecurity questions so problematic. They use information that is personal to the user and so is known by other people close to the user. These are the pool of people that hijackers with a grudge come from. The abusive ex-husband or ex-boyfriend, the shady relative, the ex-friend with an ax to grind, the friend-of-a-friend who decides to target them because they think it’s easy money. These are also the people most likely to know the answers to insecurity questions. As friends or friends of friends, they likely have access to their target’s social media. Insecurity questions are the same questions that show up on Facebook polls all the time: Name your favorite album. Your porn name is your first childhood pet plus the name of the street you grew up on. What car did you learn to drive on? What was your first job?
Not to mention what happens when a site gets hacked and their database of insecurity questions stolen. The whole point of these questions is that the answers are the same everywhere, that the user knows the answer because it is something about them. When a password is compromised, we tell people to choose a different password. What do we tell them if their insecurity question answers are compromised? Choose a new favorite teacher? Change where they went on their honeymoon?
But even without hacks, as friends or friends of friends hijackers with a grudge can also acquire this information through normal conversation.
The third major issue, and the one which stymies attempts to make insecurity questions more secure, is that the answers to these questions are ephemeral. They are questions with real answers, and those answers can and do change over time. Favorites change; inspirations change. A person’s knowledge of their past changes over time. Even the way someone spells words or refers to the same person, place, event, or thing, changes over time. And this usually happens without our even realizing it.
This means that insecurity questions are only really useful if they are available in plaintext for both ends to see: to display to the user when they log in with their password, so that they can update their answers when the answers become wrong; and to display to the tech support person who can view the answers and realize that if you were born in Maplewood you were also born in St. Louis. Or that if your favorite rapper is listed as Puff Daddy, answering P Diddy is a correct answer and that Spider-Man and Spiderman are the same superhero.
These are real things4, and real things can be referred to in different ways.
Securing the answers as if they were passwords hides this5, and by hiding it destroys the reason these questions were asked to begin with: to provide questions that the unprepared user can answer in order to gain access to their account. If the answers are secured as if they were passwords, no ambiguity is allowed in answering them, and they become for all practical purposes useless—except for account hijackers. The way that valid users respond to not knowing the password and the way that account hijackers respond to not knowing the password are very different. Hijackers can afford to be patient. They can wait weeks to find a way in. The benefit to them is the same whether they get in immediately or in a year. This is not true of the account owner, who needs to access the service now.
Of course, this sort of ambiguity also plays into social engineering attacks, since many of these questions have a limited number of likely answers.
Insecurity questions are designed to bypass not knowing a password. This is a trait shared both by the user who has forgotten their password (or lost some other access credential) and by anyone who wants to hijack the account and never knew the password. By their nature insecurity questions provide access to the account both to the forgetful and to the criminal.
If we hashed5 the answers to security questions, required users to choose strong answers, and didn’t allow them to use easily-guessable answers, then there would be no point to them. They will always be insecure, and they will always be dangerous.
- March 20, 2019: Security is hard, and 2FA is not the answer
-

Another part of the problem is trying to take the human factor out security. In this image from Homeland Security, for example, turning an in-person security check into a remote security check.
I’ve become a one-note-Cassandra about identity authentication, especially insecurity questions and their subset, out-of-wallet questions. I even tried to create an insecurity-questions tag on StackOverflow, adding the tag to several related questions in the hope of getting some outside-the-box thinking done. It failed, probably justifiably so—I’ve been on StackExchange for several years now, but really don’t understand how the system works.
Often, when this topic comes up, someone in the comments—or even the blog author—suggests two-factor authentication as the answer—even in this article at KrebsOnSecurity detailing the dangers of phone authentication. I have never done so. For one, it doesn’t even make sense. Taken literally, it’s a non-sequitur. Two-factor authentication means that the person needs to know both their password and have some other identifying factor, and insecurity questions are technically meant for when someone does not know their password.
The suggestion makes more sense, however, when you realize that the real problem is trust, and that 2FA inevitably devolves to ½FA at the drop of an appropriate sob story.
In many ways, despite the claims of incredible divides today, we trust far too much. Banks still hand out checks, meant to be given to third parties, that contain all of the information needed to drain checking accounts. Every time we write a check, we are implicitly trusting that the person we give the check to, as well as everyone in the chain of handling the check, on down to the people who trash it or shred it, can be trusted with full access to our money. And don’t think you’re above the problem because you don’t write checks; the information that matters is the information you give to every system that offers to put money into your checking account. The same information that puts money into your account can take money out of your account.
Even the last four digits of your social security number are very close to an insecurity question/answer pair. They are real information that, because everyone asks for them, everyone knows.
↑Out-of-wallet questions are among the worst: they are questions whose answers are pulled from public databases, and used to verify your identity for accessing important financial resources. You have no choice about which questions are used, the whole point of their being chosen is that they are publicly available, and they are used specifically for accessing your most important financial information.
↑Even calling the process password recovery is wrong: the process is for resetting a password, not recovering one. If the process ever provides the previous password, this means the service stores the passwords insecurely. It also means that someone can hijack your account without any immediate indication it has been hijacked.
↑Even the fictional ones.
↑Passwords are secured by hashing them. Hashing is a process that encodes a piece of text in such a way that the text cannot be decoded. Hashing is a one-way process: text can be hashed, but not unhashed. This means that even if someone hacks a server’s account database and steals all the usernames and password hashes, they cannot use that database to learn what the passwords are, except by brute-force trying every possible password.
The way that the server knows to give you access when you type your password is that the server hashes the password you typed, and then compares that hash to the hash it has stored. If they match, you get access.
If the typed password differs from the original in any way, even by a single letter or an additional space or by letter case, the hashes will not match, and there is no indication of how close the guess was. This makes hashing completely useless for insecurity questions.
↑
- Blog Entries Tagged “security questions”: Bruce Schneier at Schneier on Security
- Schneier on Security blog posts tagged as about insecurity questions.
- Good Security Questions: Garry Scoville
- “In reality, there are few if any GOOD security questions. People share so much personal information on social media, blogs, and websites, that it is hard to find questions that meet the five criteria.”
- It’s no secret: Measuring the security and reliability of authentication via ‘secret’ questions: Stuart Schechter, A. J. Bernheim Brush, and Serge Egelman (PDF)
- “Acquaintances with whom participants reported being unwilling to share their webmail passwords were able to guess 17% of their answers. Participants forgot 20% of their own answers within six months. What’s more, 13% of answers could be guessed within five attempts by guessing the most popular answers of other participants…”
- New Research: Some Tough Questions for ‘Security Questions’: Elie Bursztein at Google
- “Our findings, summarized in a paper that we recently presented at WWW 2015, led us to conclude that secret questions are neither secure nor reliable enough to be used as a standalone account recovery mechanism. That’s because they suffer from a fundamental flaw: their answers are either somewhat secure or easy to remember—but rarely both.” (Techmeme thread)
- Posts Tagged: secret questions: Brian Krebs at Krebs on Security
- Krebs on Security posts about insecurity questions.
- Why don’t the answers to “security questions” need to be stored securely? at Stack Overflow
-
 “Given that security questions and answers often allow a user access to an account in a workaround way, without requiring the password, why are they allowed to be stored in plain text?”
“Given that security questions and answers often allow a user access to an account in a workaround way, without requiring the password, why are they allowed to be stored in plain text?”
More insecurity questions
- Security is hard, and 2FA is not the answer
- Is 2-factor authentication the magic bullet in security? Not unless we solve the real problem, which is that people always take the easy way out—and that includes service providers.
- Are insecurity questions designed to help hackers?
- Insecurity questions are being modified to make them easier to hack and harder to remember. It’s as if they’re designed to help hackers and frustrate forgetful account owners.
- Insecurity Questions enable harassment and abuse
- Insecurity questions are designed specifically to let someone who does not have your password access your account without having to talk to a human. The idea is that that person will be you after you forget your password, but the computer does not care. Anyone or anything with that information can access your account.
- Allow men to impersonate exes, transgender activists say
- Some transgender activists want banks to reduce the security on bank accounts, enabling abusive exes to access their victims’ bank accounts.
- Mat Honan should read Mimsy
- “Because the last four numbers of your SSN are what businesses ask for, they are all that a criminal sometimes needs to use your cash or credit.”
- Two more pages with the topic insecurity questions, and other related pages
More passwords
- Security is hard, and 2FA is not the answer
- Is 2-factor authentication the magic bullet in security? Not unless we solve the real problem, which is that people always take the easy way out—and that includes service providers.
- Allow men to impersonate exes, transgender activists say
- Some transgender activists want banks to reduce the security on bank accounts, enabling abusive exes to access their victims’ bank accounts.
- Insecurity questions on phones and at banks
- How important are the last four digits of your social security number? That and a high school yearbook can get a hacker your bank account.
- The most popular passwords at school
- We are still lying about passwords to our community. What are the most popular first words in passwords?
- Embarrassing password tricks
- Never trust anyone over 30 characters.
